
In a shocking turn of events, Apple’s flagship product, the iPhone, has come under intense scrutiny following allegations that it may have been used to leak top secret messages from the United States military. As concerns surrounding digital privacy, cybersecurity, and national defense intensify, the role of commercial technology in handling classified government information is being called into question.
### A Breach of National Trust

The latest controversy stems from reports indicating that sensitive U.S. military communications were allegedly intercepted via compromised iPhones. While Apple has long prided itself on the security features embedded in its devices, this incident suggests that even the most secure consumer tech can be vulnerable under certain circumstances. Critics argue that over-reliance on commercial technology for sensitive military operations opens doors to foreign surveillance and cyber-espionage.
### The Core of the Controversy
According to unnamed sources within the Department of Defense, multiple iPhones used by military personnel were potentially exploited through either software vulnerabilities or third-party applications. These vulnerabilities allegedly allowed unauthorized access to high-level discussions, strategic plans, and classified intelligence communications.
The controversy erupted after a series of messages containing military-grade information were leaked on dark web forums and intelligence-sharing networks, prompting an immediate federal investigation. Although investigators have yet to release their full findings, early assessments suggest that the iPhone may have played a key role in the breach.
### Apple’s Response

In response to the growing criticism, Apple issued a brief statement denying any intentional wrongdoing. The company emphasized its longstanding commitment to user privacy and security, citing advanced encryption protocols and regular security updates as examples of its dedication. “We are actively cooperating with relevant authorities to investigate any potential misuse of our technology,” the statement read.
However, Apple’s assurances have done little to quell the public backlash. Lawmakers, cybersecurity experts, and privacy advocates are calling for greater transparency and urging the tech giant to disclose any known vulnerabilities that could have contributed to the leak.
### Implications for National Security
The potential involvement of iPhones in leaking top-secret military messages has far-reaching implications for national security. If proven true, the breach could compromise U.S. military strategies, endanger troops overseas, and weaken the country’s position in geopolitical conflicts.
Experts warn that modern warfare is not only fought on battlefields but also in cyberspace. “In today’s digital age, securing military communications is as important as securing weapons systems,” said Dr. Marcus Lang, a former NSA analyst and cybersecurity consultant. “If adversaries can access our communications through everyday devices, it gives them a strategic advantage without ever firing a shot.”
### The Role of Consumer Technology in the Military
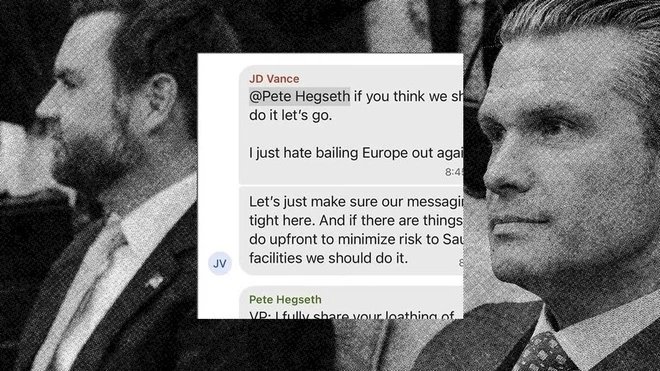
The incident has reignited debate over the use of consumer-grade devices like iPhones in military settings. While smartphones offer convenience, versatility, and powerful communication capabilities, they may lack the hardened security infrastructure found in specialized military-grade equipment.
Over the years, the military has integrated more commercial technology into its operations to streamline communication and enhance operational flexibility. However, critics argue that this dependence may come at a cost. In this case, it appears that convenience may have trumped caution.
### International Ramifications
Beyond domestic concerns, the alleged iPhone breach has sparked interest among international intelligence communities. Allies are reportedly reassessing the security of their own communications in collaboration with U.S. forces, while adversaries may seek to exploit any discovered weaknesses.
China and Russia, two nations known for their advanced cyber capabilities, are suspected to have been monitoring U.S. digital communications for years. If they were involved in this incident, it would mark a significant escalation in cyber warfare tactics, potentially justifying retaliatory action or sanctions.
### Legislative Action on the Horizon
In the wake of the controversy, members of Congress have begun drafting legislation aimed at regulating the use of commercial technology in military operations. Proposals include mandatory security audits of devices used by government personnel, restrictions on certain applications, and enhanced funding for cyber defense initiatives.
Senator Rachel Thompson, chair of the Senate Intelligence Committee, has called for a bipartisan hearing. “The American people deserve answers. We cannot allow a consumer device—no matter how popular—to compromise our national security,” she stated during a press briefing.
### Public Reaction and Media Coverage

As the story continues to unfold, public reaction has been mixed. Some users have expressed outrage over the perceived failure of Apple to safeguard user data and military information. Others argue that the fault lies with improper usage protocols within the military, rather than the device itself.
Media outlets have seized upon the scandal, with headlines ranging from “Apple Under Fire” to “iPhone at the Center of National Security Crisis.” Tech publications are diving into the technical aspects, speculating on how the breach occurred and whether similar incidents could happen in the future.
### Experts Weigh In
Cybersecurity professionals have pointed out several possible vectors for the leak, including phishing attacks, unsecured Wi-Fi networks, outdated software, and compromised third-party apps. Some have also raised concerns about state-sponsored malware that targets iOS vulnerabilities, often unknown to the public until exploited.
“Security is never absolute,” said Lina Patel, a cybersecurity researcher at MIT. “Even Apple’s walled garden can be breached, especially when facing adversaries with virtually unlimited resources and motivation.”
### Moving Forward: Policy and Prevention
In response to the growing crisis, the Pentagon has reportedly issued new internal guidelines restricting the use of smartphones for sensitive communications. A task force has also been assembled to review all existing protocols and assess future risks.
The military is expected to invest heavily in secure communications infrastructure, including encrypted satellite phones and custom-built devices with enhanced protection measures. At the same time, Apple is being urged to increase collaboration with national security agencies to proactively identify and resolve security risks.
### The Fragility of Digital Privacy
This incident underscores the fragile nature of digital privacy in an interconnected world. As more sensitive activities migrate online, from government operations to private conversations, the potential for catastrophic data breaches increases. Trust in technology is being tested like never before.
Privacy advocates worry that incidents like this could lead to an erosion of civil liberties, as governments may respond with sweeping surveillance measures. Balancing national security with individual privacy remains a delicate act, especially when consumer tech blurs the lines between personal and professional use.
### Conclusion: A Wake-Up Call for the Tech Industry
The controversy surrounding iPhones and the alleged military message leak serves as a stark reminder of the double-edged sword that technology represents. While smartphones revolutionize communication and enhance operational efficiency, they also introduce significant security risks—especially when used in high-stakes environments like national defense.
As investigations continue, one thing is clear: stronger safeguards must be put in place. Tech companies, governments, and users alike must collaborate to ensure that innovation does not come at the cost of national security. This scandal may very well become a turning point in how the military—and society as a whole—views and manages digital security in the modern age.


